hackers
Explore the anonymous world of criminal hackers, hacktivists and playful attention-seekers.
Introduction: What is Cold Email and Its Importance in Business?
The Power of Cold Email for Business Growth Building Relationships with Potential Clients Cold email provides businesses with an opportunity to establish meaningful connections with potential clients. By crafting personalized and compelling messages, businesses can grab the attention of recipients and spark their interest. This initial contact can pave the way for further communication and relationship-building, ultimately leading to conversions and increased sales. Try For Free Streamline Your Outreach Efforts with Cold Email Software
By Steve R. Anderson3 years ago in 01
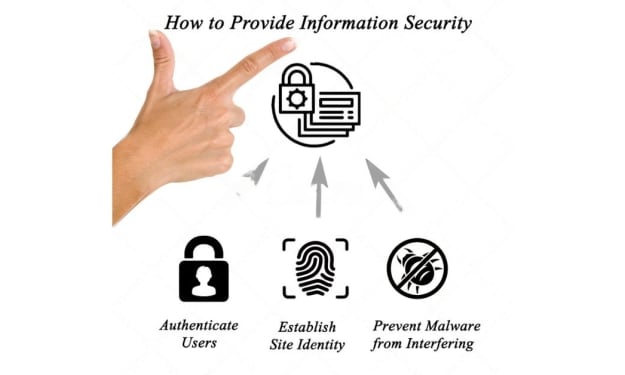
Information Security Manager Remote Tasks
As a remote information security administrator, you are primarily responsible for protecting an organization's data and maintaining its security systems against potential threats or risks. This includes a combination of strategic planning and day-to-day operations, which can range from developing security policies and procedures to managing a team of information security professionals to responding to security incidents.
By Ahtasham Rao3 years ago in 01
The Top Cyber Security Threats You Need to Know About in 2023
Introduction: As technology continues to advance, so do the threats that come with it. In today's digital age, cyber security has become a critical concern for individuals and businesses alike. With the rise of online threats such as phishing scams, ransomware attacks, and data breaches, it's more important than ever to protect your personal and business data from cyber criminals. In this guide, we'll cover the top cyber security threats you need to know about in 2023 and provide strategies for staying protected.
By GelStories3 years ago in 01
The future of crypto...
Cryptocurrency is gaining popularity and showing potential to become an integral part of our financial future. It represents a truly innovative concept, which is a rarity in itself. Think of Bitcoin as a decentralized system of record-keeping, where you pay individuals in Bitcoin to verify those records. Each day brings forth a new set of records, and this process is self-enforcing, immune to external or central authorities. Essentially, it presents itself as a new form of money, investment asset, and even a new kind of computer.
By Ajay Abraham3 years ago in 01
A Man at War
William T. Sherman’s recognition precedes him. Writing to his brother in the penultimate year of the Yankee Civil battle, the Union soldier Eb Allison observed that ‘battle, to achieve success, is an element that does not admit of any dilly-dallying approximately it.’ This remark may well function as a summation of William T. Sherman’s technique to a conflict that, as a long way as public opinion is involved, defined his profession and his life, but not always in a tremendous way. Sherman’s reputation is in lots of approaches ‘unenviable’, Brian Holden Reid notes in his creation of this formidable biography, consisting as it does in large part of exaggerated negatives: ruthlessness, heartlessness, and brutality. Informed by means of the evaluations of those Confederates whom he defeated at the time (and their progeny ever considering) Sherman’s famous photo has ended up emblematic of all we worry in modern conflict, of all we worry in ourselves as humans with a propensity in the direction of destruction.
By Dominic Odey3 years ago in 01
WhatsApp secretly listening to you in your sleep
barely any days back a viral tweet by a specialist working in Twitter which expressed that WhatsApp receiver was being used despite the fact that he was sleeping soundly. This made apprehension among individuals that WhatsApp was keeping an eye on them through the receiver around evening time.
By olasunkanmi Ijaola3 years ago in 01
Java interface document evolution history: liberate your hands step by step
At the beginning, the front and rear ends are separated, and the back end has to inform the front end of the information of the interface to facilitate the front end to call. That's all the information you need to provide, just write it in word, so you have this interface document:
By Nell Jonas3 years ago in 01