hackers
Explore the anonymous world of criminal hackers, hacktivists and playful attention-seekers.
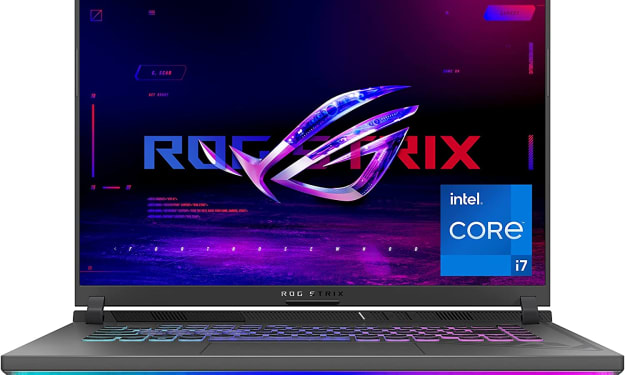
Unleash Your Gaming Potential with the ASUS ROG Strix G16 (2023) Gaming Laptop
Hello everybody! If you're looking to take your gaming experience to the next level, the ASUS ROG Strix G16 (2023) Gaming Laptop is the ultimate choice. As a passionate gamer, I can't help but be thrilled about the incredible features and specifications this laptop has to offer. Let's dive into each parameter and understand why they are vital for an exceptional gaming experience.
By Andrii Kutasevych3 years ago in 01
(MMOBizOpps) Easy Affiliate Commissions review
Are you looking to earn easy affiliate commissions online without the hassle of product creation or technical skills? Look no further! In this comprehensive training program, we provide you with a proven formula and step-by-step instructions to help you drive sales and generate profits quickly. Whether you're a beginner or an experienced marketer, our system offers a turnkey solution with built-in offers and a done-for-you funnel, eliminating the need for hosting, customer service, or complex setups.
By outofboxreview3 years ago in 01
GOOGPT-4 Review: the Power of AI for Efficient Marketing and Content Creation
Do you have trouble coming up with original ideas for your website and marketing materials? Maybe you put too much time and effort into starting from scratch while developing content. If you identify with this predicament, GOOGPT-4 is the answer you seek.
By outofboxreview3 years ago in 01
Top 5 Ways to Earn Money through Cloud Computing
Cloud computing has rapidly developed throughout the years and has demonstrated to be a boon for small entrepreneurs as well as enormous aggregates. The term has been settling in the market for 10 years, however, it picked up acknowledgment and prominence as of late. Cloud computing has all the information, messages, applications, and considerably more in virtual software like Google Drive and Dropbox, which are speedy and safe to access regardless of time and geological boundaries. Intel Security researched a sample universe of 1400 IT security experts. This research report uncovered that out of this sample, 93% of experts utilize hybrid (Private/Public) cloud computing services to operate their business operations. Cloud computing can be deployed universally in practically no time and offer the most extreme flexibility, agility, and cost-sparing IT operations to business for progressively profitable and consistent development.
By Moses Ainoje3 years ago in 01
Love Across Time
Once upon a time, in a small town nestled by a shimmering river, there existed a tale of love that defied the boundaries of time. In the quaint village, whispers of an ancient legend passed down through generations spoke of a mystical portal hidden deep within the enchanted woods. According to the legend, this portal had the power to unite two souls from different eras.
By Precious Ahaneku3 years ago in 01
Earn $$$$ Bounties
ChatGPT Bugbounty prompts get the link at the end of this article! 🔥📢 Attention all bug bounty hunters! I have an incredible story to share with you that involves a game-changing tool that has transformed my bug bounty hunting journey. It’s all about ChatGPT prompts, and believe me, this AI-powered gem has turned the tables in my favor, helping me uncover hidden vulnerabilities and earn some serious cash along the way. 😎💰
By Nikki Clam3 years ago in 01
Meta Issues Mea Culpa Over Facebook Friend Request Glitch
Meta Issues Mea Culpa Over Facebook Friend Request Glitch Social media giant Facebook has been in the news lately, and not for the right reasons. The company has been facing criticism over its handling of user data and its role in spreading fake news. Now, Facebook is once again in the spotlight, this time for a glitch that caused users' friend requests to be sent to people they didn't intend to send them to.
By Tech For Ever3 years ago in 01