hackers
Explore the anonymous world of criminal hackers, hacktivists and playful attention-seekers.
Black Basta Ransomware Gang Exposed: Internal Chat Logs Leak Online
Leaked Chat Logs Expose Internal Conflict and Operations An unknown leaker has released what they claim to be an archive of internal Matrix chat logs belonging to the Black Basta ransomware operation. The leaked information sheds light on the gang’s internal operations, conflicts, and possible motivations behind their cybercriminal activities.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
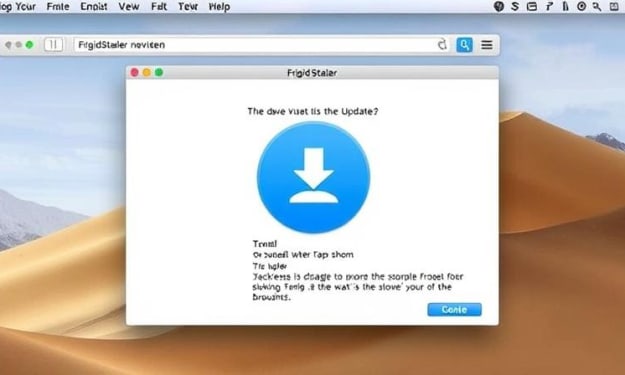
Beware of Fake Updates: FrigidStealer Malware Targets Mac Devices
The FakeUpdate malware campaigns are becoming increasingly complex, with two additional cybercrime groups, TA2726 and TA2727, now involved in delivering a new macOS infostealer malware called FrigidStealer. These threat actors are running campaigns that distribute malware via fake browser update notifications, affecting not only Mac users but also Windows and Android users.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Cybercriminals Use Invisible Unicode to Mask JavaScript in Phishing Attacks
A new JavaScript obfuscation technique leveraging invisible Unicode characters to represent binary values is actively being used in phishing attacks. This novel method, first disclosed in October 2024, has been quickly adopted by threat actors targeting affiliates of an American political action committee (PAC).
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Australian Fertility Services Giant Genea Hit by Security Breach
One of Australia’s largest fertility service providers, Genea, has confirmed a security breach after detecting suspicious activity on its network. The company revealed that unknown attackers had gained unauthorized access to its systems, prompting an urgent investigation to determine the extent of the breach and its potential impact on patients.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Microsoft App-V Tool Becomes New Weapon for Chinese Hackers to Avoid Detection
Introduction Cybersecurity researchers have recently uncovered a sophisticated cyber-espionage campaign conducted by the Chinese Advanced Persistent Threat (APT) group known as Mustang Panda. The group has been found leveraging Microsoft Application Virtualization Injector (MAVInject.exe) as a Living-Off-the-Land Binary (LOLBIN) to stealthily inject malicious payloads into legitimate processes, thereby bypassing antivirus detection mechanisms. This evasion technique was uncovered by security analysts at Trend Micro, who have tracked this threat actor under the codename “Earth Preta.”
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Hackers Target Insight Partners in Latest High-Profile Cyberattack
Introduction New York-based venture capital and private equity firm Insight Partners recently disclosed that it suffered a cybersecurity breach in January 2025 following a sophisticated social engineering attack. The firm, which manages over $90 billion in regulatory assets and has invested in more than 800 software and technology companies worldwide, confirmed the incident in a public statement issued on Tuesday.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
MiTM and DoS Attacks Enabled by Critical Flaws in OpenSSH
Introduction OpenSSH has recently released security updates to address two critical vulnerabilities that expose SSH servers to machine-in-the-middle (MiTM) and denial-of-service (DoS) attacks. One of these vulnerabilities has remained undiscovered for over a decade. The security research team at Qualys identified and reported these issues to OpenSSH maintainers, demonstrating their potential exploitability.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
How to hack my girlfriend's phone remotely without access. AI-Generated.
Don't waste your time and just use the below. Ensuring the security of your partner's smartphone is vital to protect their personal information and maintain privacy. Both Android and iOS devices are susceptible to various hacking techniques. By understanding these methods and implementing preventive measures, you can help safeguard your partner's device.
By ryan buffet12 months ago in 01
How to hack my girlfriends phone remotely. AI-Generated.
Ensuring the security of your partner's smartphone is vital to protect their personal information and maintain privacy. Both Android and iOS devices are susceptible to various hacking techniques. By understanding these methods and implementing preventive measures, you can help safeguard your partner's device.
By ryan buffet12 months ago in 01
How to hack my partner's phone without access: Common vulnerabilities & safeguarding it
Understanding how hackers can remotely access and control smartphones is crucial for implementing effective security measures. Both Android and iOS devices are susceptible to various hacking techniques. By recognizing these methods, you can take proactive steps to protect your device and personal information.
By ryan buffet12 months ago in 01
How to remotely access & control an android phone without access
Remotely accessing and controlling an Android phone is a powerful capability that can be utilized for various legitimate and ethical purposes, such as providing technical support, managing devices within an organization, or assisting family members with their devices. It's imperative to emphasize that any form of unauthorized access to personal devices is illegal and unethical. This comprehensive guide explores 20 legitimate methods and tools for remotely accessing and controlling an Android phone, ensuring compliance with legal and ethical standards.
By ryan buffet12 months ago in 01