hackers
Explore the anonymous world of criminal hackers, hacktivists and playful attention-seekers.
Cash for Gold in Australia: Tips to Get the Best Price for Your Gold
Gold has always been a valuable asset, and selling it can be a great way to get some extra cash. Whether you have old jewelry, coins, or gold bars, selling your gold at the right time and to the right buyer can help you get the best price. If you are in Australia and thinking about selling gold, this guide will help you understand the process, prepare your gold, and maximize your returns.
By TimeandGold12 months ago in 01
How to Screenshot on MacBook Pro: A Comprehensive Guide for Every User
How to Screenshot on MacBook Pro: A Comprehensive Guide for Every User Capturing a screenshot on your MacBook Pro might seem like a simple task, but did you know there are multiple ways to do it, each tailored to different needs?
By Aman Saxena12 months ago in 01
Apple Removes iCloud End-to-End Encryption in the UK Following Government Pressure
Apple has made the controversial decision to no longer offer its optional iCloud end-to-end encryption feature, Advanced Data Protection (ADP), in the United Kingdom. The move follows demands from the UK government for a backdoor to access encrypted cloud data, sparking a heated debate over digital privacy, national security, and the future of encrypted communications in the country.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Hackers Target Craft CMS: CISA Confirms Code Injection Flaw Exploitation
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has issued a warning about a remote code execution (RCE) vulnerability in Craft CMS that is being actively exploited in attacks. The flaw, tracked as CVE-2025-23209, is classified as high severity with a CVSS v3 score of 8.0 and affects Craft CMS versions 4 and 5.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
Crypto Giant Bybit Hit by $1.46 Billion ETH Cold Wallet Heist
In a shocking cyber heist, cryptocurrency exchange Bybit has confirmed that an unknown attacker has stolen over $1.46 billion worth of cryptocurrency from one of its Ethereum (ETH) cold wallets. The incident, now regarded as the largest crypto theft in history, has sent shockwaves throughout the digital asset industry.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
US Telecom Networks Hacked: Chinese Cyber Spies Use Sophisticated Malware
The Chinese state-sponsored hacking group known as Salt Typhoon has been identified as using a custom utility called JumbledPath to stealthily monitor network traffic and potentially capture sensitive data. These cyberattacks have targeted major U.S. telecommunication providers, raising significant concerns about national security and data privacy.
By WIRE TOR - Ethical Hacking Services12 months ago in 01
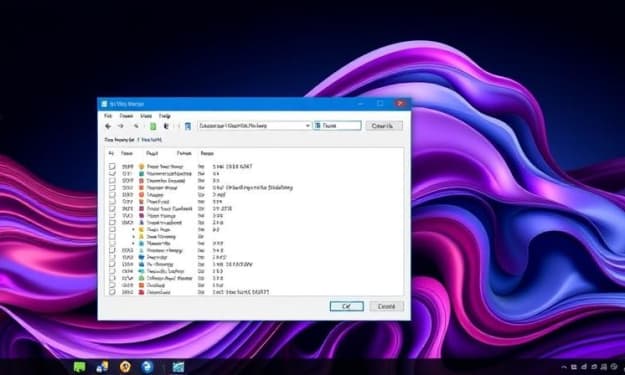
WinRAR's New Update Boosts Privacy by Removing Windows Metadata
Introduction WinRAR, one of the most widely used file archivers and compression tools for Windows, has just received a significant update with the release of version 7.10. This new update introduces several features aimed at improving performance, usability, and security. Among these, one of the most notable changes is the ability to strip sensitive metadata from the Mark-of-the-Web (MoTW) alternate data stream, increasing privacy for users who frequently download and share files.
By WIRE TOR - Ethical Hacking Services12 months ago in 01