how to
How tos for tech whizes and luddites alike; tips, tricks and shortcuts to optimize your computer, smartphone or internet mastery.
Premium Snapchat Bio Ideas: 21 Best Premium Snapchat Bio Ideas
Are you looking for intriguing and appealing Snapchat bio ideas to make your profile stand out from the crowd? Because Snapchat bio is all about making a good impression and engaging more people over the internet. Sometimes, most people see your bio and photos before deciding whether or not to follow you.
By Intelligent Creatorabout a month ago in 01
What is Slack Huddle And How You Can Use It?
A Slack Huddle is a comparable idea to Clubhouse and Twitter Spaces in that there's genuinely not a proper gathering time or greeting. The entire thought is that individuals can basically "drop in" to a Huddle at whatever point.
By Intelligent Creatorabout a month ago in 01
Understanding WS2813 LED Strips and LED Strip Light Technology
LED strip lighting is a widely used lighting format found in residential, commercial, and creative environments. Its thin profile, flexibility, and low power requirements have made it suitable for applications where traditional fixtures are impractical. Over time, LED strip light technology has evolved to include more advanced control methods, including digitally addressable systems such as WS2813.
By charliesamuelabout a month ago in 01
Understanding Flexible LED Wall Washers and Wallwasher Lighting
Wallwashing is a well-established architectural lighting technique used to evenly illuminate vertical surfaces such as walls, facades, and large structural elements. The primary goal of wallwasher lighting is to create uniform brightness across a surface, reducing harsh shadows and visual distractions while enhancing the perception of space and texture.
By charliesamuelabout a month ago in 01
How to Stop Wasting Leads
Most teaching businesses don't actually have a lead problem. They have a follow-through problem. People reach out. They call. They text. They DM. And then the teacher responds late, or vaguely, or like the person is interrupting their life. Or they go back and forth for three days trying to find a time. Eventually the lead disappears, and the teacher concludes that marketing doesn't work.
By Destiny S. Harrisabout a month ago in 01
The Accessibility Crisis of 2026: What No One Wants to Admit
Every January, the internet fills with glossy predictions about the future - tech trends, workplace trends, fashion trends, AI trends. But there’s one category that rarely makes the list, even though it affects millions of people every single day:
By Tracy Stineabout a month ago in 01
How to Mask Your IP for Privacy and Security
Every click, every search, every download leaves a digital footprint, and websites, advertisers, and sometimes even hackers can trace you through your IP address. The good news is that you don’t have to stay exposed. Hiding your IP address is simpler than most people think, and doing it correctly can protect your privacy, secure your data, and even give you access to content that was previously unavailable. Next, we’ll take a look at the different ways to hide your IP and how to choose the method that works best for you.
By Swiftproxyabout a month ago in 01
The Real Methods of Gmail Hacking: How Accounts Are Compromised and How to Protect Yourself. AI-Generated.
The Illusion of Invulnerability A Gmail account is more than just an email inbox—it's a digital passport to our online identity, connecting our social media, financial services, cloud storage, and professional communications. Many users operate under the dangerous assumption that Google's security is impenetrable, but the reality is that human error and sophisticated attacks create vulnerabilities that hackers exploit daily. This comprehensive guide will explore the actual methods used to compromise Gmail accounts, examine the tools employed by malicious actors, and provide actionable strategies to fortify your digital presence against these threats.
By Alexander Hoffmannabout a month ago in 01
The Real Methods of Outlook Hacking: How Accounts Are Compromised and How to Protect Yourself. AI-Generated.
Microsoft Outlook, with over 400 million active users, is a prime target for cybercriminals. This article isn't a guide to hacking; it's a forensic look at the real methods attackers use to compromise Outlook accounts. By understanding these techniques, you can build an impenetrable defense. We will delve into the dark underbelly of cyber threats, expose the tools used (for educational awareness only), and equip you with the knowledge to shield your digital life.
By Alexander Hoffmannabout a month ago in 01
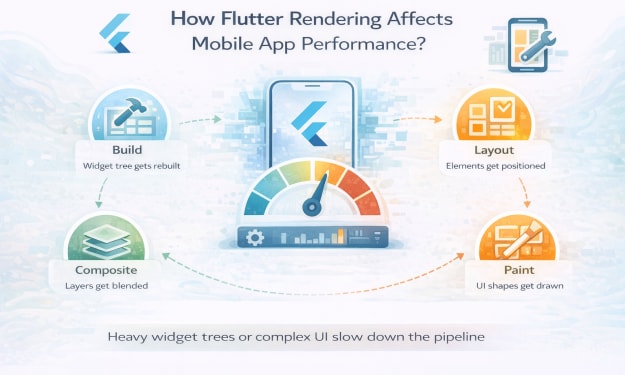
How Flutter Rendering Affects Mobile App Performance?
I still remember the first Flutter app I shipped to production. The UI felt smooth. Almost suspiciously smooth. Animations flowed like they were rehearsed. Then a user emailed support saying the app felt “heavy” after ten minutes of use. Not broken. Just tired.
By Mary L. Rodriquezabout a month ago in 01