cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
An Introduction to EnOcean: Advantages, Uses & More
Buildings, workplaces and homes are becoming smarter than ever before, with more sensors, automation and data being included within them. This presents a new challenge as many smart technologies rely on wiring, batteries and ongoing maintenance, which adds cost, disruption and environmental impact to many buildings.
By Simon Rhodes5 days ago in 01
The Battery of Trust: How Phone Charging Habits Relate to Honesty in Location Sharing. AI-Generated.
Hey there. Over years of building location-sharing tools, I've noticed a pattern that rarely gets discussed: the link between a phone's battery life and the health of a relationship built on digital trust. It sounds odd, right? But think about it. The most common technical excuse for a location tracker failing is, "My phone died." While sometimes true, this dead battery can often be a symptom, not just a cause—a digital tell that signals a deeper disconnect.
By Olivia Martinez6 days ago in 01
The API Security Risks Healthcare Leaders Can’t Afford to Overlook
Introduction: Why Healthcare APIs Are a Critical Risk Area Healthcare organizations increasingly rely on APIs to connect electronic health records (EHRs), patient portals, telemedicine platforms, and external service providers. This connectivity improves care coordination and operational efficiency, but it also expands the digital attack surface in ways many organizations underestimate.
By Sam Bishop7 days ago in 01
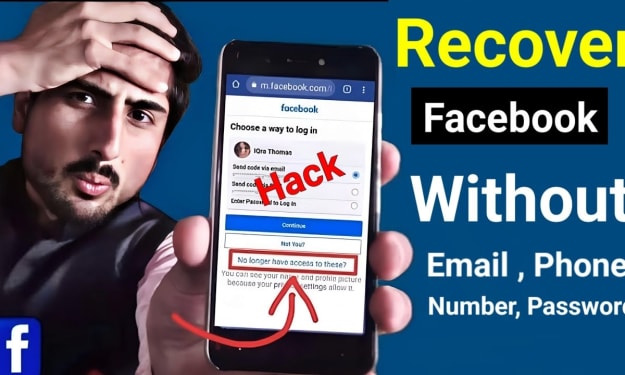
The Top 10 Reasons Why Hackers Target Facebook Accounts: A Complete Guide to Methods, Malware, and Protection. AI-Generated.
The Billion-Dollar Black Market of Stolen Identities A Facebook account is more than a social profile—it’s a digital identity, a repository of personal connections, memories, and often, a gateway to other online services. This immense value has made Facebook accounts a prime target for cybercriminals worldwide. But what truly drives hackers to invest time and resources in compromising these accounts? This in-depth article explores the top motivations, reveals the real methods and tools used, and provides a robust defense blueprint to protect your digital life.
By Alexander Hoffmann8 days ago in 01
The Complete Guide to Hack Gmail Password in 2026: Understanding Threats and Protection. AI-Generated.
Disclaimer: This article is for educational and informational purposes only. Unauthorized access to computer systems, including email accounts, is illegal under laws like the Computer Fraud and Abuse Act (CFAA) in the United States and similar legislation worldwide. This guide aims to help users understand threats to better protect their accounts, not to facilitate hacking.
By Alexander Hoffmann8 days ago in 01
How Missing API Visibility Creates Security Gaps in FinTech
Introduction In the fast-paced world of financial technology, APIs power almost every transaction, integration, and customer interaction. They connect internal services, third-party partners, and external platforms to deliver seamless experiences. However, with this complexity comes a critical risk: missing API visibility. When organizations cannot see or fully understand all their API endpoints, undocumented APIs, or dynamic connections, hidden security gaps emerge that can be exploited by attackers.
By Sam Bishop10 days ago in 01
Exploring the FinTech Innovation Behind Buy Now Pay Later Solutions
Introduction In recent years, Buy Now Pay Later (BNPL) solutions have emerged as one of the most influential innovations in the FinTech ecosystem. By allowing users to split payments into manageable installments, BNPL platforms have changed how consumers interact with digital commerce. What appears simple on the surface is actually powered by a sophisticated mix of financial logic, modern software architecture, and advanced data technologies. Understanding the innovation behind BNPL solutions offers insight into why they have gained rapid global adoption and how they continue to evolve.
By Nayel Basim Al Shehhi11 days ago in 01
OWASP Top 10 2025: Key Changes You Should Know
Introduction The OWASP Top 10 list is one of the most widely used security frameworks in the world. Every update represents a shift in the real threats organizations face based on global incident data, community research, and evolving attack patterns. The 2025 edition brings meaningful changes that reflect how modern applications are built, integrated, and deployed.
By Sam Bishop11 days ago in 01
Configure KeyLocker for JarSigner using the DigiCert KSP Library
Prerequisites Before configuring KeyLocker for JarSigner, please ensure you have the following components and environment set up. Each of these is necessary and plays a role in establishing a contracted, secure, engaging signing environment.
By Anna Shipman13 days ago in 01
Navigating Cryptocurrency Asset Recovery
The challenging environment of digital asset theft and loss has given rise to a specialized sector focused on recovery. This field consists of companies with distinct operational models, from direct investigation to technical support and foundational analytics. The following outlines five notable entities often referenced in this space, categorized by their primary function.
By Milan Roberts13 days ago in 01