cybersecurity
Our personal, digital, national and military security depend on a safe cyber space.
The Hacker
A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means. Though the term hacker has become associated in popular culture with a security hacker – someone who utilizes their technical know-how of bugs or exploits to break into computer systems and access data which would otherwise be unavailable to them – hacking can also be utilized by legitimate figures in legal situations.
By AKHIL SENGAR4 years ago in 01
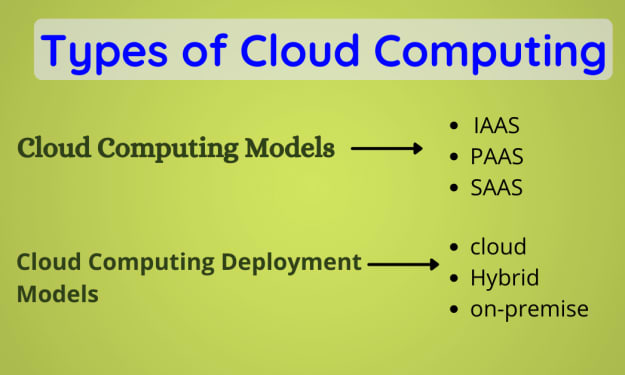
Why Your Business Needs Managed It Services? - UpRaqx
Technology is an integral part of a business now, and it is rapidly transforming the world of business in which data is the key to unlocking all the potential possibilities. Data fuels the growth of modern business. It is one of the most important assets of the company. However, as the technology goes with rapid changes, the IT requirements are also evolving continually. And along with that, security threats, especially with data, are also increasing rapidly. The continuous rise in the number of securities and data breaches on a cloud and on-premises is challenging to everyone. Sometimes even a breach can cost companies a loss in reputation and a huge loss in dollars. And therefore, in this scenario, Managed IT services come into the picture. After taking advantages of managed IT services, you can save your valuable time and run your business more smoothly.
By Neil Martin4 years ago in 01
What Really Happens During A Cyber Attack?
The world observers one digital assault at regular intervals (source). However, over 95% of the cyberattacks are because of client mistake. This measurement shows that individuals fail to really see how a digital assault functions. Digital assaults sent off by unscrupulous programmers and malignant crooks assault mobiles, PCs, different PCs, and whole organizations. The goal is to debilitate PCs and take touchy information. A few aggressors take our PCs and different assets to send off different assaults on other unwary organizations. Online protection specialists counter these crooks through devices and preparatory techniques.
By Nagesh palkar4 years ago in 01
Why do you need Zero Trust for your organization?
As businesses continue to embrace hybrid cloud environments, the need for stronger security management becomes a need of the hour. Futurism Managed Security Acceleration Services powered by IBM leverages a deny-by-default security policy and authorization for each connection. Futurism Managed Security Acceleration Services bring in the right mix of industry-leading IBM security technology and tools to offer security that is uncompromised and unparalleled using a Zero Trust Architecture to provide protection against coming-of-age cyber threats including new strands of Ransomware, social engineering hacks, and multi-prong attack tactics.
By Futurism Technologies4 years ago in 01
Cybersecurity Career
The answer is a resounding YES. Not only is the market growing fast but so are the job openings and this is all reflected in high paying jobs forecasted to keep growing until 2030 and probably beyond. Read on to find out how and why this market has become such a force.
By John Smith4 years ago in 01
Setup Your own VPN for Family: Pros and Cons
Network security has become necessary for everyone, not just for businesses as people generally used to think. It’s not just big corporations that are facing cyberattacks and data breaches. Especially with the advent of smart devices, attackers are now constantly targeting home internet users due to the lack of security measures taken by them. Hackers often sneak and gain access to your devices connected to the home network if you do not take enough precautions.
By Samantha Markas4 years ago in 01
External Cloud Automotive Cyber Security Services Market is expected to Reach USD 6.42 billion & Grow 17.1% CAGR, Size, Share, Trends, Growth & Forecast by 2028 - HARMAN International, Continental AG
External Cloud Automotive Cyber Security Services Market report contains detailed information on factors influencing opportunities, demand, growth, challenges, drivers, and restraints. It provides detailed information about the structure of global and regional industries. The report also includes data on research & development, new product launches, product responses from the global and local markets by leading players. The structured analysis offers a graphical representation and a diagrammatic breakdown of the External Cloud Automotive Cyber Security Services Market by region.
By nutanpatel4 years ago in 01